The Operating Microscope in Dentistry
2 May 2025
Applied Cybersecurity for Dental Practices: Challenges, Regulatory Framework, and Protection Strategies
Introduction to Cybersecurity for Dental Practices
The digital transformation has profoundly reshaped the practice of dentistry worldwide. Dental clinics—like the broader healthcare sector—rely increasingly on digital technologies for patient record management, medical imaging, appointment scheduling, billing, and communication.
While this digitalization enhances efficiency and the overall quality of care, it simultaneously exposes healthcare structures to significant cybersecurity vulnerabilities. Every new interconnected system or database expands the potential attack surface, offering more points of entry for malicious actors. There is therefore an inherent tension between the operational benefits of digitalization and the imperative of security.
The protection of health data—by nature extremely sensitive—is a critical concern. Dental records contain confidential personal and medical information whose compromise can have devastating consequences: unauthorized access, data theft or alteration, disruption of care, significant financial losses, reputational damage, and legal liability for practitioners.
The value of these data extends far beyond their financial worth on illicit markets. It encompasses the fundamental trust between patient and practitioner, the integrity of individual medical histories, and the risk of misuse for identity theft or targeted manipulation.
Securing this information is therefore not merely a technical or legal obligation—it is a matter of public trust and professional ethics at the very heart of healthcare systems.
This article provides an in-depth analysis of the specific cybersecurity challenges faced by dental practices globally. It explores the threat landscape, applicable regulatory frameworks, prevention and protection strategies, incident response measures, and available resources and support mechanisms.
I. The Cyber-Threat Landscape and Specific Vulnerabilities in Dental Practices
Although dental practices are often small or medium-sized structures, they represent prime targets for cybercriminals due to the nature of the data they handle and several structural vulnerabilities inherent to their operations.
A. Why Dental Practices Are Attractive Targets
Several factors explain why dental practices are particularly appealing to cyberattackers.
1. The High Value of Health Data
Medical records consolidate permanent and highly sensitive personal information, such as medical histories, identification numbers, prescriptions, and diagnostic results.
These data sets can be sold on the dark web for a price significantly higher than financial information—in some cases up to 50 times more valuable—because of their permanence and their potential use in complex fraud schemes or identity theft.This high commercial value provides a strong economic incentive for cybercriminals to target healthcare organizations, including dental practices.
2. Inherent Risks of Small and Medium-Sized Practices
Most dental practices operate as small or medium-sized enterprises (SMEs) and therefore share the vulnerabilities common to smaller organizations:
• They rarely employ dedicated IT or cybersecurity staff.
• Security budgets are often limited compared with large hospitals or healthcare networks.
• Outdated systems are frequent. The continued use of obsolete hardware or unsupported operating systems (such as Windows 7 or older imaging software) creates known, unpatched vulnerabilities.
Operational dependency on digital systems further increases exposure.
A ransomware attack can completely paralyze the clinic, forcing appointment cancellations and disrupting the continuity of patient care.
Many practices lack a formal emergency response plan or tested backup strategy, leaving them unable to recover efficiently after an incident.
The absence of regular, verified data backups is among the most critical weaknesses observed across small healthcare entities.
This combination of high-value data, limited cybersecurity resources, and strong dependence on digital systems forms what experts call a “triangle of vulnerability.”
From an attacker’s perspective, dental practices represent high-impact, quick-return targets, especially for ransomware groups who exploit the urgent need to recover patient data and resume clinical operations.
3. The Human Factor as the Weakest Link
A significant share of successful cyberattacks—estimated at around 70% in the healthcare sector and similarly applicable to dental environments—can be traced back to human error.
Insufficient training and awareness among staff members remain major contributors to breaches.
Common risky practices include:
• Using weak or reused passwords;
• Poor management of user access rights;
• Failure to recognize phishing or social-engineering attempts.
Cybercriminals actively exploit these weaknesses to gain initial access to systems or credentials, emphasizing that cybersecurity is not only a technological issue but also a matter of culture, education, and daily vigilance.
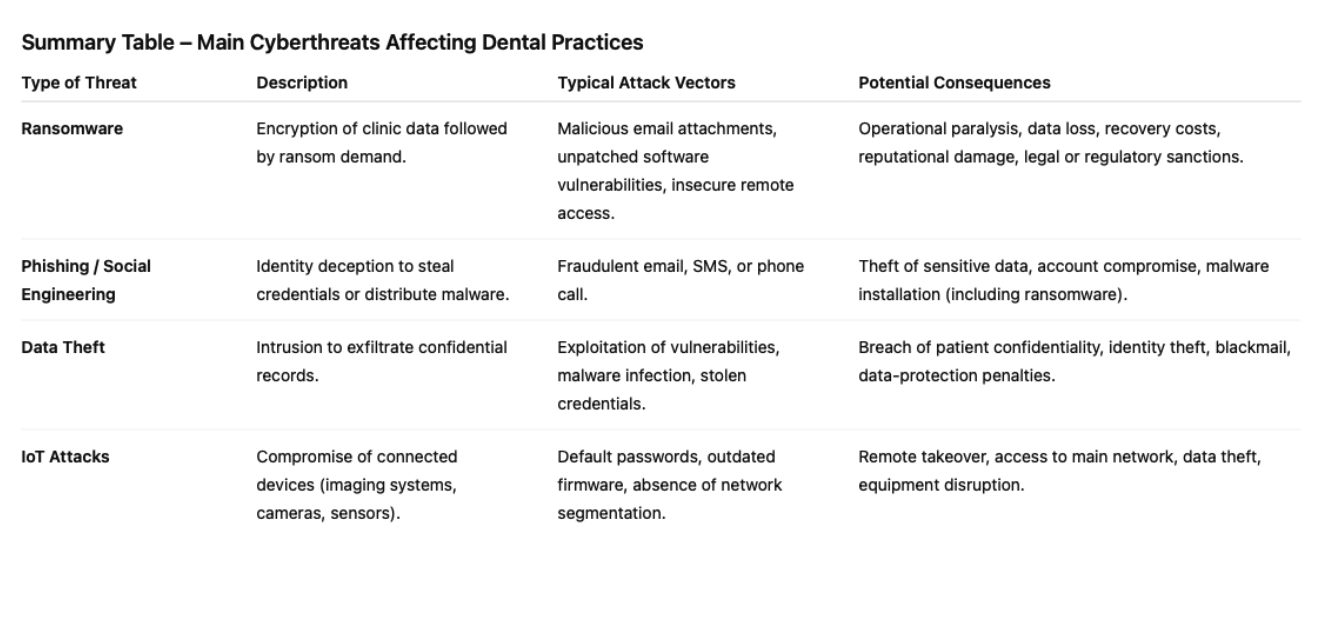
B. Common Types of Cyberattacks
Dental practices are exposed to a variety of cyberattacks, some of which are particularly frequent and damaging.
1. Ransomware Attacks
Ransomware is among the most feared threats in healthcare.
This type of malicious software encrypts the clinic’s data, rendering it inaccessible, and then
demands a ransom—usually in cryptocurrency—in exchange for a decryption key.
The consequences can be severe: complete paralysis of the practice’s information system, forced return to paper records, large-scale appointment cancellations, and in some cases, threats to publicly release stolen data if payment is refused.
Across Europe and internationally, national cybersecurity agencies (such as ENISA in the EU, CISA in the United States, and CERTs in many countries) have reported a sharp rise in ransomware incidents targeting the health sector.
Typical impacts include encrypted patient histories, radiographs, and billing files, sometimes resulting in a total shutdown lasting days or weeks.
The official guidance from cybersecurity authorities worldwide is clear: never pay the ransom.
Payment does not guarantee data recovery and encourages further criminal activity.
2. Phishing and Social Engineering
Phishing remains one of the most common and effective attack vectors.
It relies on psychological manipulation to deceive users into revealing confidential information (such as usernames or passwords) or downloading malware.
Attackers often impersonate legitimate entities—government agencies, suppliers, or colleagues— through fraudulent emails, SMS messages, or phone calls.
Studies show that more than half of healthcare professionals are unable to reliably identify a fraudulent email.
Successful phishing attempts can lead to the theft of patient records, compromise of user accounts, and even total system paralysis.
3. Other Relevant Threats
In addition to ransomware and phishing, dental practices may fall victim to:
• Data theft, through unauthorized intrusions into databases and exfiltration of sensitive health information;
• Denial-of-Service (DDoS) attacks, which, though less common for small practices, aim to make online services—such as clinic websites or appointment-booking portals—temporarily unavailable;
• Compromise of connected medical devices (IoT), such as imaging systems or smart sensors, when default passwords, outdated firmware, or lack of network segmentation expose them to external access.
C. Emerging Threats and Future Trends
The cyber-threat landscape is constantly evolving, with new attack vectors appearing and existing techniques growing increasingly sophisticated.
1. The Internet of Things (IoT) in Dental Practices
The rapid spread of connected devices—the Internet of Things (IoT)—within dental environments introduces new and often underestimated attack surfaces.
Smart dental chairs, digital X-ray systems, monitoring sensors, surveillance cameras, and even connected televisions in waiting rooms can all become entry points for cyber-intrusions.
These devices are typically less secure than traditional computers, often shipped with weak default passwords and limited update mechanisms.
Once compromised, an IoT device can serve as a pivot for attackers to infiltrate the practice’s main network, exfiltrate sensitive data, or disrupt the operation of other connected equipment.
Securing such devices requires several essential measures:
• isolating IoT equipment on a separate network segment;
• changing default credentials immediately upon installation;
• applying firmware and software updates without delay;
• disabling any non-essential features or network services.
Obsolete or unsupported systems—already a recurring issue for workstations—represent not only a technical weakness but also the symptom of a wider gap between the fast pace of technologicalchange and the limited adaptation capacity of small healthcare structures.
This underlines the need for structural, financial, and training support mechanisms to maintain adequate security standards globally. National or regional initiatives—such as the European Commission’s Digital Europe Programme or national health-security modernization plans—serve as models for broader professional outreach and capacity building among small, independent healthcare providers.
2. Artificial Intelligence (AI): A Tool for Both Attack and Defense
Artificial Intelligence (AI) is becoming a double-edged sword in cybersecurity.
On the offensive side, cybercriminals are increasingly leveraging AI to enhance the precision, automation, and personalization of their attacks:
• generating highly realistic phishing emails and fake websites;
• creating deepfakes for identity theft or fraud;
• automating password-cracking and credential-stuffing campaigns;
• coordinating large-scale attacks against networks of connected medical devices.
According to recent global surveys, more than four out of five organizations have already encountered cyberattacks amplified by AI capabilities.
On the defensive side, however, AI provides powerful tools to strengthen protection:
• faster and more accurate threat detection through behavioral analytics;
• automated incident response and containment mechanisms;
• intelligent decision support for security teams and system administrators.
Yet, AI systems themselves can become targets of attack, particularly when models or datasets are manipulated, leading to biased or malicious outputs.
The introduction of both IoT and AI into dental practices—while enabling major innovation in patient care—will exponentially increase the complexity of cybersecurity management.
Practitioners will have to secure not only their traditional IT systems but also a growing ecosystem of interconnected and intelligent devices, requiring specialized expertise and constant vigilance —a significant challenge for small and medium-sized healthcare organizations.
II. Regulatory and Normative Framework: Obligations and Recommendations
The management of cybersecurity and data protection in dental practices is governed by a complex but coherent set of laws, regulations, and professional guidelines issued by national and international authorities.
While navigating this framework may be challenging for small and medium-sized practices, understanding it is essential to ensure data protection, legal compliance, and patient trust.
A. The General Data Protection Regulation (GDPR)
Enforced since 25 May 2018, the General Data Protection Regulation (Regulation (EU) 2016/679) is the cornerstone of personal data protection across the European Union.
It applies directly to all healthcare providers, including dental practices, and has also influenced many privacy frameworks around the world, such as Brazil’s LGPD, California’s CCPA, and international standards like ISO/IEC 27701.
Applicability and Core Principles for Health Data
The GDPR governs all processing of personal data—whether digital (management software, electronic health records) or on paper.
Because of their intimate and identifying nature, health data are classified as special category data (formerly known as “sensitive data”) and benefit from reinforced protection.
Their processing is generally prohibited, except in specific cases outlined in Article 9 of the GDPR—such as when necessary for preventive medicine, medical diagnosis, treatment, or healthcare system management.
Dental practices must therefore respect the fundamental principles of the GDPR:
• Lawfulness, fairness, and transparency in processing activities;
• Purpose limitation: data may be collected only for explicit and legitimate purposes;
• Data minimisation: only strictly necessary information should be processed;
• Accuracy: data must be up to date and correct;
• Storage limitation: data must not be kept longer than necessary;
• Integrity and confidentiality: security and access control are mandatory;
• Accountability: the practice must be able to demonstrate its compliance at all times.
Specific Obligations for Dental Practices
1. Maintain a Record of Processing Activities (ROPA):
Each practice must maintain an internal record listing all data processing operations (e.g.,patient management, billing, appointment scheduling).
Many data protection authorities—such as France’s CNIL, Spain’s AEPD, or Germany’s
BfDI—provide templates to assist with this task.
2. Inform Patients Transparently:
Patients must be informed clearly and accessibly about the collection and use of their data and their rights (access, rectification, erasure, restriction, portability, objection).
This information can be displayed in the waiting room, on the practice’s website, or included in consent and intake forms.
3. Conduct a Data Protection Impact Assessment (DPIA):
Required whenever data processing is likely to pose a high risk to individuals’ rights and freedoms—for instance, in cases involving large-scale handling of health data or use of cloud-based imaging systems.
4. Manage Data Breaches:
In the event of a security incident—such as data leakage, loss, or unauthorized access—the practice must notify its supervisory authority (e.g., CNIL, ICO, or national DPA) within 72 hours if the breach may affect individuals’ rights.
When the risk is high, the affected patients must also be informed promptly and transparently.
5. Regulate Relationships with Third Parties (Processors):
All third-party service providers (software vendors, hosting companies, online booking platforms, etc.) must offer sufficient guarantees regarding security and data protection.
These relationships must be formalized through written contracts compliant with Article 28 of the GDPR, defining each party’s responsibilities.
6. Appoint a Data Protection Officer (DPO), if applicable:
Required when the core activities involve large-scale processing of sensitive data or systematic monitoring of individuals.
For large group practices or dental networks (for example, handling more than 10,000 patient records), appointing a DPO—either internally, externally, or jointly—is considered a best practice even when not strictly mandatory.
Penalties for Non-Compliance
Failure to comply with the GDPR can result in severe sanctions:
• Administrative fines of up to €20 million or 4% of global annual turnover, whichever is
higher;
• Criminal penalties in certain jurisdictions for data misuse or negligence;
• Reputational and financial damage due to loss of patient trust or public exposure.
European supervisory authorities have already sanctioned several healthcare providers for security failures leading to medical data breaches—for example, a €1.5 million fine imposed in a French case for insufficient data protection measures.
B. Health Data Hosting and International Security Standards
The question of health data hosting is crucial worldwide and governed by specific regulatory requirements to ensure confidentiality, integrity, and availability of medical information.
1. Certification Requirements for Health Data Hosts
In France, the “Hébergeur de Données de Santé” (HDS) certification is a legal requirement for any organization hosting personal health data on behalf of third parties.
At the international level, equivalent frameworks exist to guarantee similar standards of protection — including ISO/IEC 27001 for information security management and ISO/IEC 27701 for privacy management.
In the United States, the HIPAA Security Rule serves a comparable purpose.
These certifications or accreditations aim to ensure a high level of data protection, covering:
• Physical security of data centers;
• Logical and network security of systems;
• Access control and traceability;
• Backup, recovery, and business continuity procedures;
• Data reversibility at the end of service contracts.
They are typically granted following independent audits by accredited bodies and are valid for limited periods, requiring renewal to ensure continued compliance.
2. Implications for Dental Practices
When a dental practice chooses to outsource the storage or processing of patient health data — for example, by using cloud-based practice management software, online backup services, or document-sharing platforms — it must ensure that the chosen provider complies with recognized international or national standards such as HDS, ISO/IEC 27001, or GDPR-compliant hosting within the EU/EEA.
It is the responsibility of the practice to:
• Verify the validity and scope of the provider’s certification;
• Confirm that data are hosted within jurisdictions offering adequate legal protection;
• Include detailed data protection clauses in service contracts (aligned with Article 28 of the GDPR).
Outsourcing data processing does not exempt the practice from its own responsibilities as the data controller.
A common misconception is that delegating hosting also delegates accountability — in reality, clinics must exercise continuous due diligence and ensure contractual, technical, and operational compliance by all partners.
3. Choosing Compliant Software and Backup Solutions
Dental management software must fully comply with data protection and security standards.
When offered as a cloud-based (SaaS) solution, the publisher or hosting provider must hold appropriate certifications (HDS, ISO/IEC 27001, or equivalent).
Selection criteria should include not only functionality and usability but also verifiable guarantees in terms of security, traceability, and regulatory compliance.
Best practice recommends hosting patient health data within the European Economic Area (EEA) or in other countries that provide adequate data protection under GDPR adequacy decisions.
This also strengthens data sovereignty, an increasingly important concept in healthcare digitalization policies around the world.
C. National and International Guidelines
Beyond the GDPR and health data hosting standards, numerous national and supranational bodies issue rules and recommendations to guide healthcare professionals in securing their information systems.
1. National Health Information Security Frameworks
In France, the General Security Policy for Health Information Systems (PGSSI-S), developed by the Agence du Numérique en Santé (ANS), serves as a reference framework for protecting digital health data.
At the European level, its equivalent is the ENISA Health Sector Security Framework, and internationally, it aligns with best practices such as those outlined in ISO/IEC 27002 and NIST SP 800-66.
These frameworks provide:
• Mandatory security requirements for health data processing;
• Practical guides to help professionals achieve adequate protection levels;
• Guidance for evaluating and managing cyber risks in medical environments.
2. Recommendations from National Cybersecurity Agencies
Most countries maintain a national cybersecurity authority (e.g., ANSSI in France, CISA in the United States, BSI in Germany, NCSC in the UK).
These agencies publish extensive guides and best practices that are directly applicable to healthcare professionals.
Notable examples include:
• “Cyber Hygiene Guidelines” – a set of essential measures for all organizations;
• Guides on ransomware prevention, incident response, and crisis management;• Risk analysis methodologies, such as EBIOS Risk Manager or the NIST Cybersecurity Framework;
• Promotion of the Zero Trust security model, emphasizing verification and least-privilege principles.
These recommendations provide valuable, actionable frameworks for dental practices seeking to strengthen resilience and improve operational security.
3. The Role of National Health Digital Agencies and Incident Response Centers
Agencies responsible for health digital transformation, such as France’s ANS, Spain’s Red.es, or Italy’s AGID, play a key role in promoting secure digital healthcare ecosystems.
They provide:
• Guides and toolkits for secure data management;
• Funding and audits for security improvements;
• Technical frameworks on identity verification, electronic signatures, and interoperability.
Their affiliated Computer Emergency Response Teams (CERTs) or Computer Security Incident Response Teams (CSIRTs), such as CERT Santé in France or CERT-EU, operate 24/7 to assist healthcare entities during cyber incidents and issue regular threat intelligence reports specific to the medical sector.
4. Professional Bodies and Sectoral Guidance
Professional dental associations and national dental councils (such as the Ordre National des Chirurgiens-Dentistesin France, or similar institutions across Europe and the Americas) also contribute to cybersecurity awareness.
They issue specific recommendations such as:
• Good cybersecurity practices for dental professionals;
• Practical IT security handbooks for small private practices;
• Guidance on using secure health messaging systems (e.g., encrypted professional mail solutions compliant with national health networks).
These bodies emphasize the importance of:
• Continuous staff training and awareness;
• Careful selection and contractual management of digital service providers;
• Promoting a culture of security across the entire care team.
5. Guidance from Data Protection Authorities
The Commission Nationale de l’Informatique et des Libertés (CNIL) is France’s supervisory authority for personal-data protection.
Comparable bodies exist in every jurisdiction — for example, the ICO in the United Kingdom, AEPD in Spain, Garante Privacy in Italy, BfDI in Germany, and the Office of the Privacy Commissioner in many non-EU countries.
These authorities ensure the application of privacy and data-protection regulations such as the GDPR and provide extensive guidance to help professionals achieve compliance.
They regularly publish practical resources, including:
• Guides on GDPR compliance tailored to healthcare professionals;
• Technical recommendations on topics such as password management, backup procedures, and website security;
• Information on data-retention periods (for example, medical records must typically be stored for twenty years after the last patient visit);
• Self-assessment checklists to help small healthcare practices evaluate their level of compliance.
6. A Need for Simplification and Harmonization
The coexistence of numerous frameworks and guidelines — including the GDPR, HDS certification, PGSSI-S, and recommendations from agencies such as ANSSI, ANS, CNIL, and professional bodies like the ONCD — can appear complex for small and medium-sized dental practices.
While this multiplicity aims to achieve the highest level of protection, it can paradoxically become an obstacle to compliance for smaller organizations with limited human and financial resources.
There is therefore a growing need for simplified, practical, and accessible tools that translate legal and technical requirements into actionable steps for healthcare professionals.
Despite this complexity, there is strong synergy and coherence among all the authorities’ key messages:
• the critical importance of regular and tested data backups,
• the use of robust password and access-control policies,
• continuous staff training in cybersecurity awareness, and
• preparedness for incident response and recovery.
This convergence reinforces the effectiveness and clarity of the core recommendations, even if the dispersion of information sources can still create uncertainty for practitioners seeking a single, unified roadmap for cybersecurity compliance.
III. Cybersecurity Prevention and Protection Strategies for Dental Practices
In the face of an increasingly complex threat landscape and a demanding regulatory environment, dental practices must adopt a proactive approach to cybersecurity, combining robust technical safeguards with rigorous organizational practices.
The goal is to develop a genuine security culture shared by every member of the team.
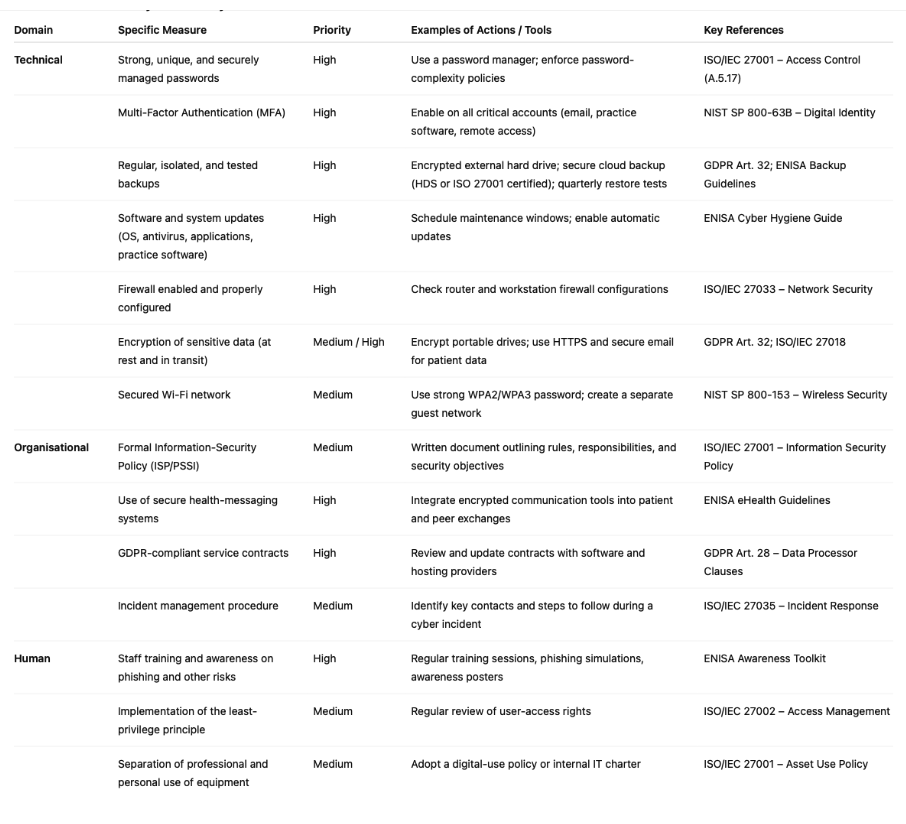
A. Fundamental Technical Measures
The foundation of effective protection lies in the implementation of a secure and resilient IT infrastructure.
1. Securing the Infrastructure
Every workstation and server must be properly protected.
Operating systems and software should be regularly updated with the latest security patches.
Reliable, up-to-date antivirus solutions must be installed, and system configurations hardened to limit vulnerabilities.
Automatic session locking after periods of inactivity is a simple yet effective control to prevent unauthorized access when users are away from their desks.
If the practice has a Wi-Fi network, it must be secured using strong encryption (WPA2 or preferably WPA3). The router’s default password must be changed immediately, and broadcasting of the network name (SSID) can be disabled.
Creating a separate guest Wi-Fi network, isolated from the clinic’s internal network, is strongly recommended for patients and visitors.
A firewall—hardware or software—is essential to filter communications between the practice’s network and the Internet, blocking intrusion attempts and controlling inbound and outbound data traffic.
Built-in firewalls such as Microsoft Defender Firewall (Windows) or equivalent systems on macOS or Linux must be enabled and properly configured.
2. Access and Identity Management
Strong password and identity management is fundamental.
Passwords must be long (at least 12 characters), complex (including uppercase, lowercase, numbers, and special symbols), and unique for each account or application.
Using a password manager is recommended to create and securely store strong passwords without relying on written notes or unsecured documents.
Passwords should be changed periodically and never stored directly in web browsers.
Multi-Factor Authentication (MFA)—combining something the user knows (password), something they possess (one-time code, physical key), or something they are (biometricauthentication)—should be activated whenever possible, particularly for systems containing sensitive data, professional software, and online services.
According to international studies, MFA can prevent up to 99% of unauthorized access attempts.
Access rights should follow the principle of least privilege: each user (dentist, assistant, receptionist) should have only the permissions necessary for their specific tasks.
3. Backup Policy
Reliable, frequent backups are the most effective protection against data loss, whether caused by hardware failure, human error, or cyberattacks such as ransomware.
Backups should be:
• Regular (daily for critical data) and automated whenever possible;
• Stored on multiple media types (external drives, NAS servers, or cloud storage);
• Diversified, following the “3-2-1 rule”: at least three copies of data, on two different media, with one stored offsite.
If cloud backups are used, the provider must be secure, GDPR-compliant, and certified (for example, HDS, ISO/IEC 27001, or equivalent).
Local backup drives should be physically disconnected from the main network after each operation to prevent ransomware from encrypting them.
It is equally crucial to test data restoration regularly to verify the integrity and functionality of backups.
Neglecting basic digital hygiene—such as updates or backup verification—often due to lack of time or awareness, directly exposes the practice to avoidable cyber risks.
4. Encryption of Sensitive Data
Encryption converts data into an unreadable format that can only be deciphered with the correct key.
It must be applied both:
• In transit, using secure protocols like HTTPS for all online communications and encrypted email attachments (especially if a secure messaging platform is not used);
• At rest, protecting stored data on laptops, USB drives, and backup devices through full-disk encryption or secure container solutions.
Encryption is one of the core security controls required under GDPR Article 32 and is also recommended under international standards such as ISO/IEC 27018 (cloud data protection) and HIPAA (in the U.S.).
5. Software Updates and Security Patch Management
Software developers regularly release updates to correct newly discovered security vulnerabilities.
It is essential to apply these updates systematically and promptly to every component of the information system — including operating systems, antivirus software, web browsers, professional applications, and any other tools used in daily operations.
Unpatched systems are one of the main causes of cyber incidents in healthcare.
Practices should therefore plan dedicated maintenance time to perform updates and monitor vendor advisories.
Where possible, enable automatic updates or use centralized patch-management tools to ensure timely deployment across all devices.
6. Secure Selection and Configuration of Professional Software and Specialized Equipment
B. Organisational and Human Measures
Technology alone is not enough; effective security also depends on clear processes and well-trained personnel.
1. Developing an Information-Security Policy (ISP)
Even for a small practice, formalising an Information-Security Policy—sometimes called an Information-System Security Policy (ISSP or PSSI)—is a vital step.
This strategic document, drafted by the lead practitioner (with external guidance if needed), defines:
• the security objectives of the clinic,
• the rules and procedures to follow,
• the roles and responsibilities of each staff member, and
• the incident-response process.
It should be based on a risk analysis specific to the practice, regularly reviewed, and updated.
Even a concise version constitutes a formal commitment to security and reassures patients that their data are handled responsibly.
2. Continuous Training and Staff Awareness
Front-desk staff, dental assistants, and practitioners are on the front line against cyber threats.
Regular training sessions and short awareness reminders are essential.
Key topics should include:
• recognising phishing or fraudulent emails,
• creating and managing strong passwords,
• workstation security and safe Internet use,
• proper use of secure health-messaging platforms, and
• how to report suspicious incidents.
Educational resources can include webinars from national or regional health-digital agencies, interactive tools such as cyber-awareness escape games, simulated phishing campaigns to test vigilance, and awareness posters displayed in staff areas.
3. Secure Communication
The use of secure health-messaging systems (for example, encrypted professional email solutions integrated into national health networks) is mandatory in many jurisdictions for exchanging personal health information between healthcare professionals and with patients through officialhealth portals.
Such systems ensure end-to-end encryption and verified sender identity.
Basic confidentiality rules must also be applied—for instance, never including a patient’s name on unprotected documents travelling with prosthetics or dental models.
These small habits uphold professional secrecy and patient privacy.
4. Management of Service Providers and Subcontractors
Dental practices frequently rely on external vendors for software, data hosting, IT maintenance, and online appointment services.
It is essential to verify each provider’s GDPR or equivalent compliance and to formalise the relationship with a written contract that includes the data-processing clauses defined in Article 28 of the GDPR (or its international counterpart).
Such contracts must clearly specify each party’s security obligations, responsibilities, and reporting procedures in the event of a data breach.
5. General Cyber Hygiene
Simple digital-hygiene rules should be applied by everyone:
• avoid using professional computers for personal activities;
• stay alert when browsing the web;
• systematically refuse non-essential cookies on non-professional sites;
• maintain physical security of offices and equipment (locked rooms, access control);
• apply secure disposal procedures when retiring old computers or storage media, including irreversible data erasure or certified destruction.
These practices complement technical controls and are essential to maintaining both data confidentiality and regulatory compliance.
IV. Cybersecurity Incident Management and Business Continuity
Despite all preventive measures, zero risk does not exist.
It is therefore imperative that every dental practice be prepared to react swiftly in the event of a cybersecurity incident and to maintain continuity of operations.
The absence of a tested Incident Response Plan (IRP) and Business Continuity Plan (BCP) can turn an already serious event into a potentially devastating crisis for the organization.
A. Detection, Analysis, and Immediate Response
Recognising the Warning Signs
Quick detection is critical to limiting impact.
Common indicators of compromise include:
• Unusual system slowdowns;
• Suspicious error messages;
• Inaccessibility of files (sometimes renamed with strange extensions);
• On-screen ransom demands;
• Abnormal network traffic or bandwidth usage.
First Response Actions
1. Isolate affected systems:
The most urgent measure is to disconnect any suspected or infected devices from the practice’s network (unplug Ethernet cables, disable Wi-Fi).
This prevents the attack—especially ransomware—from spreading to other connected workstations or servers.
2. Do not power off the compromised system (unless advised by an expert):
While instinct may be to shut the computer down, doing so can erase valuable volatile information stored in memory (RAM) that is essential for later forensic analysis.
Network isolation takes priority over shutdown.
3. Contact professionals and authorities:
Engage cybersecurity specialists or your IT service provider as soon as possible.
For major incidents, reach out to the relevant national CERT or CSIRT (for example, CERT Santé in France, CERT-EU, or your country’s incident-response centre).
Public awareness platforms—such as Cybermalveillance.gouv.fr in France or CISA’s reporting services in the US—can also guide practitioners to qualified experts.
4. Document the incident:
From the first signs, record every observation: discovery time, visible symptoms, on-screen messages, and any actions already taken.These notes will be vital for investigators, insurers, and mandatory notifications to regulators.
B. Developing and Implementing an Incident Response Plan (IRP)
An Incident Response Plan (IRP) formalises how the practice will react to a cyberattack.
Its existence—and its communication to all staff—ensures a coordinated, efficient response, reducing damage and downtime.
Guides published by ENISA, NIST, or national authorities can serve as models.
Key Stages of an IRP
1. Preparation
◦ Identify the clinic’s critical information assets (patient records, practice-management software, backups).
◦ Establish a small response team (e.g., lead dentist, designated assistant, IT provider).
◦ Define roles and responsibilities.
◦ Maintain a contact list including cybersecurity experts, insurers, data-protection authorities, and professional associations.
2. Detection and Analysis
◦ Confirm that a security incident has occurred.
◦ Determine its type (e.g., ransomware, phishing, data exfiltration).
◦ Assess the scope (systems and data affected) and evaluate severity.
3. Containment
◦ Implement immediate measures to stop further spread (for example, segment the network or disable compromised accounts).
4. Eradication
◦ Once contained, remove the root cause of the attack: delete malware, patch exploited vulnerabilities, revoke fraudulent access, and strengthen passwords.
5. Recovery
◦ Restore systems and data to normal operation, typically from verified clean
backups.
◦ Monitor restored systems for any signs of reinfection before reconnecting them to the main network.
6. Lessons Learned (Post-Incident Review)◦ After resolution, perform a post-incident analysis to understand what happened, evaluate the effectiveness of the response, and identify improvements to both the IRP and preventive controls.
C. Crisis Communication
Effective communication management is a crucial aspect of incident response.
A well-handled communication strategy helps maintain trust, reduce confusion, and demonstrate transparency and professionalism during a crisis.
1. Internal Communication
Inform all members of the practice staff clearly about the measures being taken and the procedures to follow.
Employees must know how to respond to patient questions, avoid spreading rumours, and ensure consistent messaging.
A short internal briefing or written summary can help prevent panic and ensure coordinated actions.
2. Communication with Patients
If the data breach is likely to pose a high risk to patients’ rights and freedoms (for example, the leak of medical records or identifiable information), the GDPR obliges healthcare providers to notify the affected individuals.
This communication should be transparent, concise, and respectful — explaining:
• the nature of the incident;
• the potential impact on the patient; and
• the corrective measures implemented to contain and resolve the issue.
Clear and timely communication reinforces patient confidence, even in the event of a serious breach.
3. Communication with Authorities
Depending on the nature and severity of the incident, several notifications may be mandatory or strongly recommended:
• Data Protection Authority (DPA):
Any personal data breach posing a risk to individuals must be reported to the competent authority (e.g., CNIL in France, ICO in the UK, AEPD in Spain, or national equivalent) within 72 hours, in accordance with Article 33 of the GDPR.
• National Cybersecurity Agency or CERT:
For significant cybersecurity incidents, practices should report to their national Computer Emergency Response Team (CERT) or Cybersecurity Authority (such as ANSSI in France, CERT-EU, or CISA in the US). These agencies can provide technical support and situational awareness.
• Law Enforcement:
In cases involving criminal activity, filing a report with the police or national cybercrime units is encouraged to support investigation and prosecution.
Authorities such as ENISA and ANSSI publish dedicated guides on managing cyber crisis communication, offering templates and advice to prepare key messages in advance.
D. Decision on Whether to Pay the Ransom
In the case of a ransomware attack, the question of payment inevitably arises.
However, national and international authorities — including ENISA, ANSSI, CISA, and Europol — strongly advise against paying ransoms.
Paying the ransom:
• offers no guarantee that encrypted data will be restored (attackers may provide a faulty or non-functional decryption key, or none at all);
• encourages and finances criminal activity;
• does not protect against future attacks;
• may expose the organisation to legal and reputational risks if the payment breaches anti-money-laundering or sanctions regulations.
In reality, some victims face a severe ethical, financial, and operational dilemma — particularly if critical data were not backed up or are irreplaceable.
If ransom payment is considered a last resort, it should only occur after consultation with cybersecurity experts, legal counsel, and relevant authorities, and never without a parallel plan to rebuild security and restore systems safely.
E. Business Continuity and Disaster Recovery Planning (BCP and DRP)
Beyond the immediate response to an incident, it is essential to plan how the practice can continue operating — even in a degraded mode — and how it can return to normal afterwards.
Objectives
A Business Continuity Plan (BCP) aims to maintain the practice’s critical operations during a crisis (for example, handling urgent patient care), while a Disaster Recovery Plan (DRP) defines the steps required to restore all systems and processes once the incident is resolved.
Key Elements of a BCP/DRP for a Dental Practice
• Identify critical activities and data: Determine which functions and information are absolutely essential to daily operations.
• Establish manual fallback procedures: Use temporary paper-based patient records, manual appointment scheduling, or printed consent forms to ensure continuity of care during system downtime.
• Develop clear data-recovery strategies: Define restoration priorities, expected recovery times (RTOs), and acceptable data-loss thresholds (RPOs).
• Prepare a communication plan: Inform patients about service disruptions, expected recovery timelines, and temporary procedures.
• Document, share, and test the plan: The plan must be known by the entire team and tested regularly (for example, through simulation exercises) to confirm its effectiveness.
It should also be reviewed and updated following any major change or incident.
Failure to have an emergency or continuity plan is considered one of the most significant vulnerabilities identified across healthcare organizations worldwide.
F. The Role of Cyber Insurance
Subscribing to a cyber-insurance policy can complement preventive and reactive measures.
It offers financial and logistical support to help dental practices recover from an attack.
Coverage
Cyber-insurance contracts may cover a range of costs associated with a cyber incident, including:
• Fees for cybersecurity experts involved in forensic investigation and remediation;
• Costs for data and system restoration;
• Business interruption losses caused by downtime;
• Notification expenses for patients and regulatory authorities;
• Civil-liability coverage if third parties suffer harm due to a data breach.
By 2023, nearly 70% of companies in Europe had subscribed to some form of cyber-insurance policy, reflecting the growing awareness of digital risk across all sectors.
Additional Services
Some insurers also offer preventive and support services, such as:
• Vulnerability audits and risk assessments;
• Cybersecurity awareness training for staff;
• Access to a 24/7 emergency hotline for immediate assistance during an incident.
Key Points of Attention
Before signing a policy, practices must carefully review:
• Coverage limits, exclusions, and deductibles;
• The scope of indemnification (what is and isn’t reimbursed);• The insured’s obligations regarding preventive security measures, backups, and timely reporting of incidents.
Effective management of a major cyber event often exceeds the internal capabilities of a small dental practice.
This underlines the importance of relying on an external support ecosystem — including specialized IT providers, national CERTs or health-sector CSIRTs, public assistance platforms (such as Cybermalveillance.gouv.fr or equivalents), and insurance partners.
Familiarity with these actors, and knowing how and when to engage them, is a fundamental component of cyber-preparedness and overall digital resilience.
V. Resources and Support Available to Dental Practices in France
When facing cybersecurity challenges, dental practices are not alone.
Numerous public institutions and professional bodies in France — and their counterparts in other countries — offer guidance, tools, and dedicated assistance to help strengthen digital security.
The abundance of resources is a real advantage, but their diversity can sometimes make it difficult for practitioners to identify the most relevant and prioritised advice.
A. Public Organisations and Support Platforms
1. National Cybersecurity Agency (ANSSI)
The Agence Nationale de la Sécurité des Systèmes d’Information (ANSSI) is France’s national authority for cybersecurity and cyber-defence.
It is responsible for preventing, detecting, and responding to major cyber incidents across all sectors, including healthcare.
For professionals and small businesses such as dental practices, ANSSI provides a wide range of open-access resources:
• Guides and best practices:
Its flagship publication, the “IT Hygiene Guide”, details 42 essential security measures applicable to all organisations.
ANSSI also issues specialised guides on ransomware prevention, cyber-crisis management, risk analysis using the EBIOS Risk Manager method, and industrial-system security (principles of which can be adapted to connected medical devices).
• Training and awareness:
While its training programmes primarily target critical-sector professionals, ANSSI’s principles and recommendations inspire many awareness campaigns within the broader healthcare field.
Comparable agencies exist in most countries — such as ENISA (European Union), CISA (United States), NCSC(United Kingdom), BSI (Germany), and CERT-IN (India).
2. Agence du Numérique en Santé (ANS) and CERT Santé
The ANS (Digital Health Agency) coordinates the digital transformation of France’s healthcare system, ensuring security and interoperability of health information systems.
• CERT Santé:
The Health Computer Emergency Response Team operates 24/7 under the ANS.
It assists healthcare and medico-social institutions during major cybersecurity incidents and publishes regular alerts and threat bulletins.
• Documentation and training:
The ANS maintains the General Security Policy for Health Information Systems (PGSSI-S), France’s main reference framework for digital-health security.
It also releases technical guidelines, educational memos, and webinars on electronic identification and secure data exchange.
The CaRE programme (Cybersecurity Acceleration and Resilience for Healthcare Establishments) focuses on improving the sector’s maturity; although primarily aimed at larger facilities, its lessons are equally relevant for smaller practices.
3. Commission Nationale de l’Informatique et des Libertés (CNIL)
The CNIL is France’s data-protection authority and the body responsible for enforcing the GDPR.
It provides extensive guidance and templates to help professionals understand and apply privacy obligations.
Its resources include:
• GDPR guides for healthcare professionals: covering patient rights, record-keeping, DPIAs, and breach management;
• Technical recommendations: secure password creation, backup best practices, website hardening, and protection against ransomware.
Equivalent authorities exist worldwide — such as the ICO (UK), AEPD (Spain), Garante Privacy (Italy), and the Federal Trade Commission (US) for HIPAA enforcement.
4. Cybermalveillance.gouv.fr
This national awareness and victim-assistance platform supports individuals, businesses, and local authorities facing cyber incidents.
Its mission is to assist victims, raise awareness, and monitor cyber-threat trends across France.
• Victim assistance:
The platform offers an online diagnostic tool to identify the nature of an attack (e.g., phishing, ransomware) and provides tailored guidance.
It can also connect victims with certified local IT service providers capable of intervening quickly.
• Awareness and prevention:
The website hosts numerous fact sheets and quick-response guides on key topics such as phishing, ransomware, connected-device security, password management, and backups.
It also offers ready-to-use awareness kits for staff training.The platform’s popularity continues to grow, reaching over 5.4 million unique visitors in 2024.
B. Professional Bodies and Associations
1. National Dental Council (ONCD)
The Ordre National des Chirurgiens-Dentistes (ONCD) plays an important role in informing and raising awareness among its members about their ethical, legal, and cybersecurity obligations.
• Publications and Guides:
The ONCD regularly communicates through its professional newsletter, La Lettre de l’Ordre des Chirurgiens-Dentistes, which covers topics such as data protection and cybersecurity.
It also provides practitioners with dedicated resources, including the Practical Cybersecurity Guide for Independent Practitioners and the IT Security Handbook.
• Professional Support:
The ONCD collaborates with public agencies such as the ANS (Digital Health Agency) to help the profession adopt secure digital tools—for example, integrating encrypted messaging systems into dental practice software.
2. Other Professional Associations and Unions
Organisations such as the Union Française pour la Santé Bucco-Dentaire (UFSBD) and the Association Dentaire Française (ADF) also provide information and resources related to digital practice management and cybersecurity.
They often relay government and regulatory recommendations or create their own awareness materials and training programmes.
The effectiveness of this professional ecosystem depends largely on the active engagement of dental practitioners.
The existence of guides and platforms alone is not sufficient—individual and collective awareness, as well as commitment to implementing recommendations, are essential.
Professional councils and continuing-education programmes therefore play a key role in fostering that engagement.
A close collaboration between public bodies and professional representatives ensures that prevention and support messages remain adapted to the realities and constraints of private dental practices.

Conclusion
Cybersecurity has become an unavoidable priority for dental practices.
While digital transformation brings undeniable benefits in efficiency and quality of care, it also increases exposure to cyber-risks.
The high value of health data, combined with the structural vulnerabilities of small organisations, makes dental practices attractive targets for attacks whose consequences can be severe—ranging from service disruption to serious breaches of patient confidentiality.
Threats such as ransomware and phishing remain the most common, while emerging risks linked to the Internet of Things (IoT) and Artificial Intelligence (AI) further complicate the landscape.
In response, a robust regulatory framework—built around the GDPR and specific health-data- hosting requirements (HDS in France, or ISO/IEC 27001 internationally)—sets out clear obligations for practitioners regarding data protection and information-system security.
Compliance is not merely a legal necessity but also an ethical duty and a foundation of patient trust.
Cybersecurity should therefore no longer be seen as a technical constraint or unnecessary cost, but as a strategic investment essential to the long-term stability and reputation of the practice.
To navigate this complex environment, dentists can rely on a range of preventive and protective measures—technical (infrastructure hardening, access control, robust backups, encryption) and organisational (security policy, staff training, vendor management).
Developing incident-response and business-continuity plans is equally critical to minimise the impact of successful attacks.
Numerous resources and support structures—ANSSI, ANS, CNIL, ONCD, and Cybermalveillance.gouv.fr, among others—stand ready to guide healthcare professionals on this path.
Ultimately, cybersecurity in dental practices reflects the broader challenges of the digital transformation of healthcare.A constant balance must be maintained between technological innovation, the protection of personal and medical data, economic constraints, and regulatory compliance.
The future resilience of dental practices will depend not only on adopting the right technical defences but, above all, on their ability to build and sustain a true culture of cybersecurity within their daily operations.
That requires continuous vigilance, ongoing team training, agile adaptation to new threats, and active collaboration across the healthcare ecosystem to share knowledge and best practices.
Only through this commitment can dental professionals continue to practise their art with confidence—ensuring both the safety and the trust of their patients in an increasingly connected world.